Springboot actuator unauthorized access vulnerability in the Backend
Created by: Ttstcy1
Environment
Window & Ubuntu & Centos
vulnerability detail
When logged into the background

We access this interface:
ip:/api/admin/actuator/ The monitored endpoint is leaked under the actuator path。
The monitored endpoint is leaked under the actuator path。
For example, under the env path, all environmental attribute configuration information is leaked, including a large amount of server-sensitive information:
http://ip/api/admin/actuator/env The logfile path leaked the server's real-time log records:
The logfile path leaked the server's real-time log records:
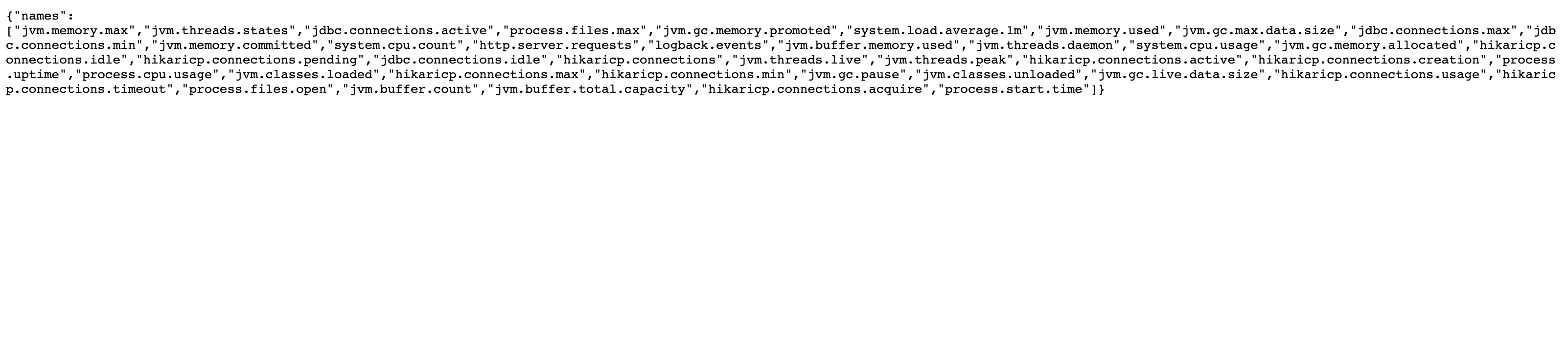
http://ip/api/admin/actuator/logfile 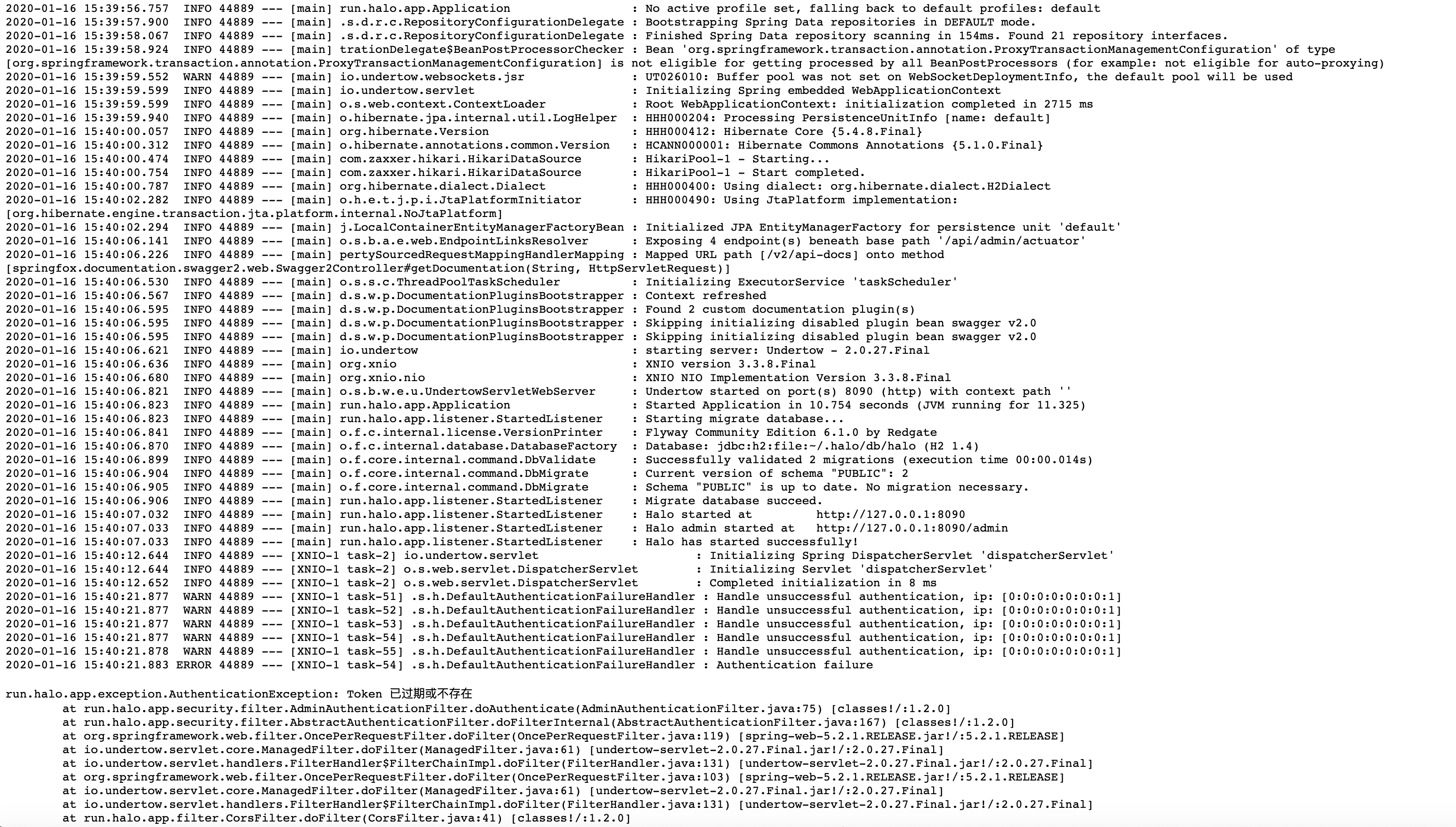 Under the metrics path, various application metrics information was leaked, such as memory usage and HTTP request counts:
Under the metrics path, various application metrics information was leaked, such as memory usage and HTTP request counts:
Reason
View source configuration file application.yaml:
 It can be found that the Actuator service is enabled by default, but the access permissions are not set.
It can be found that the Actuator service is enabled by default, but the access permissions are not set.
If Spring Boot Actuator version is too low, there is a remote code execution vulnerability,See details here:
https://www.veracode.com/blog/research/exploiting-spring-boot-actuators